Tag: SOC
SOC Fourth Defense Phase – Cyber Threat Intelligence Guide
Cyber Threat intelligence is one of the most critical concerns in the evolving threat environment of rapid day-zero attacks, cyber-criminality and espionage activities; the...
SOC First Defense – Understanding The Cyber Attack Chain – A Defense with/without SOC
This article will help you to understand the SOC modern cyber threats and the most commonly used attack surfaces behind any malware/cyber-attacks.Most times, cyber-attacks...
Diving Deeper Into Windows Event logs for Security Operation Center (SOC) – Guide
Cyber Security operations center is protecting organizations and the sensitive business data of customers.It ensures active monitoring of valuable assets of the business...
SIEM Better Visibility for SOC Analyst to Handle an Incident with Event ID
We are in a complex world where attacks are increasing day by day, so today cyber intelligence depends on SIEM as a part of infosec (security incident...
Modern CyberSOC – A Brief Implementation Of Building a Cyber Security Infrastructure
In earlier years, everyone depends on CyberSOC (including firewalls, WAF, SIEM, etc.) and the priority in building the SOC provides security, and the CIA...
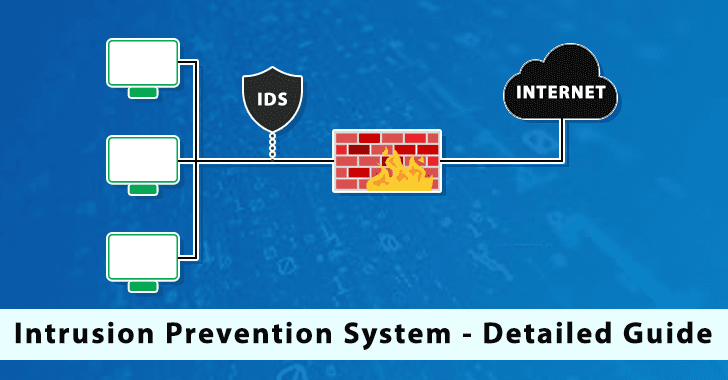
Intrusion Prevention System (IPS) In-depth Analysis – A Detailed Guide
Like an Intrusion detection system (IDS), an Intrusion prevention system (IPS) screens network traffic. In this article, we deep dive into Intrusion Prevention System...
Intrusion Detection System (IDS) and Its Detailed Working Function – SOC/SIEM
An intrusion detection system (IDS) is a type of security software designed to automatically alert administrators when someone or something is trying to compromise...
Security Information and Event Management (SIEM) – A Detailed Explanation
SIEM software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated...
Indicator Of Attack(IoA’s) And Activities – SOC/SIEM – A Detailed Explanation
What is an Indicator of Attack (IOA)IoAs is some events that could reveal an active attack before indicators of compromise become visible.The use...
How to Build and Run a Security Operations Center (SOC Guide) – 2023
Today’s Cyber security operations center (CSOC) should have everything it needs to mount a competent defense of the ever-changing information technology (IT) enterprise.This includes...










%20(1).jpg)

.jpg)




-1.webp)













