Tag: Cyber Threats
SOC Fourth Defense Phase – Cyber Threat Intelligence Guide
Cyber Threat intelligence is one of the most critical concerns in the evolving threat environment of rapid day-zero attacks, cyber-criminality and espionage activities; the...
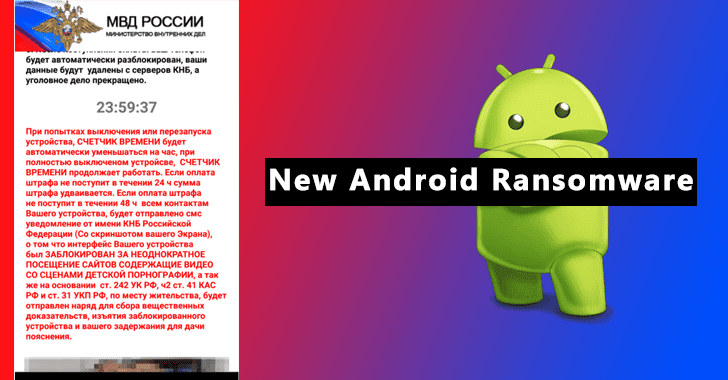
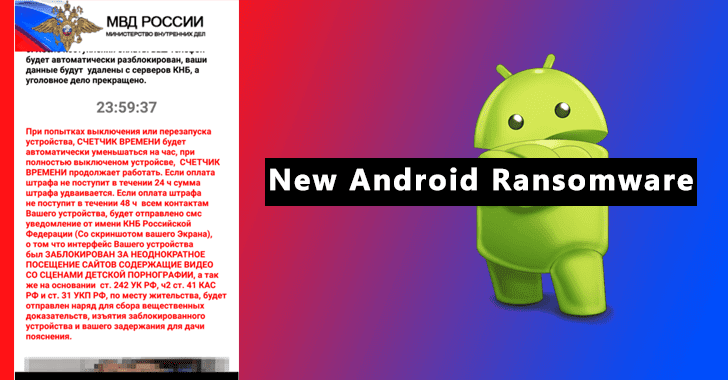
New Sophisticated Android Ransomware that Doesn’t Encrypt Files but Blocks Access to Devices
Microsoft detected new Android ransomware with new attack techniques and behavior that indicates the evolution of mobile ransomware.As we aware ransomware uses to encrypt...
Cerberus Android Banking Malware Mimic as Currency Converter App Found on Google Play
Cerberus Android banking malware found on Google play targeting Android users, particularly in Spain. Cerberus spotted first in the year 2019, it is known...
Google Patches the Critical MediaTek rootkit Vulnerability that Affects Millions of Android Devices
Google patches a critical vulnerability with MediaTek rootkit chips that affect millions of devices with chipsets from MediaTek.MediaTek is a large Taiwanese chip design...
Darknet Market AlphaBay Moderator Pleads Guilty – 20 Years of Prison
Bryan Connor Herrell, 25, AlphaBay Moderator pleads guilty for his job role in the fraudulent organization. Herrell's job role is to resolve disputes between...
Top 5 Best Cyber Attack Prevention Methods for Small Businesses With Breach & Attack...
Cyber attack prevention for Small businesses very has to get serious about their cybersecurity. Hackers are now actively Performing Targeted cyber attack due...
Most Important Consideration To Prevent Insider Cyber Security Threats In Your Organization
Insider threats are very real and make up the majority of cybersecurity attacks on enterprises. Yet, many businesses still spend most of their time...
What is Cyber Security? Why Do We Study a Cyber Security Course and...
The evolution of technology in Cybersecurity allows us to do amazing things that we only imagined doing in the past. Computers and technology have...
Gustuff Android Banking Malware Uses SMS Messages to Hack Users Device
Gustuff banking malware returns with new features, the threat actors behind Gustuff malware made changes with distribution hosts and disabled C2 infrastructure. The malware...
ATM Jackpotting – Cutlet Maker Malware Spike Around the World to Spit the Cash...
Researchers discovered a new track of ATM jackpotting attack through infamous ATM malware called “Cutlet Maker” which is now rapidly growing up around the...