DangerousPassword – Hackers Use New Attack Pattern to Infect Devices With Malware
Recently, it has been observed by JPCERT/CC that threat actors are actively targeting the cryptocurrency exchanges linked to the DangerousPassword attack campaign (aka CryptoMimic...
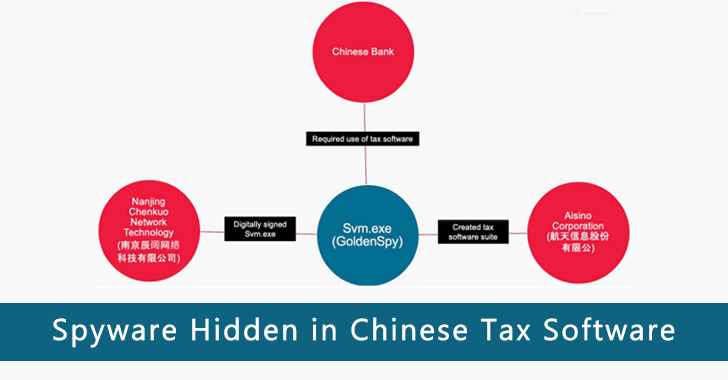
Chinese Bank Forced Companies Doing Business in China to install Malware Embed Tax Software
Advanced persistent threat (APT) campaign aims to steal sensitive information form corporations doing business in China.The malware GoldenSpy was observed by Trustwave SpiderLabs in...
Hackers Launching large-Scale phishing-as-a-service Operation with 300,000 newly created Phishing Domains – Microsoft
Large-scale well-organized phishing as a service (PhaaS) operation is uncovered recently by Microsoft. This platform helps users to customize campaigns and develop their own...
Two Massachusetts Men Arrested for Conducting SIM-swapping Attack To Steal Cryptocurrency & Social Media...
Two Massachusetts men arrested today for Conducting Nationwide SIM-swapping attack to gain login credentials of victims by resetting their login credentials.Once they got login...
Observability vs Monitoring: What’s The Difference
In a world where technology has gained traction, observability and monitoring have become common terms in software development discussions. Irrespective of how much effort...
Google Blocked Over 1.4 Million Malicious Apps From Google Play Store
Since Google bought Android 2005, its sole responsibility has been to provide the best user experience and ensure security for its users.Google Play Protect...
Migrating Data Safely: A Cyber Security Checklist for Enterprises
In many ways, you can compare data migration to moving to a new house. While the prospect of starting anew in a different environment...
Eight Foolproof Methods of Securing Your Website
Alongside their own vigilance, the security of Internet users largely depends on a website's security precautions. While there's a lot of methods that can...
Ensiko – A PHP Based Web Shell with Ransomware Capabilities Attacks PHP Installation
Researchers observed a new PHP web shell dubbed Ensiko with ransomware capabilities that attack PHP installed on platforms such as Linux, Windows, macOS, and...
Patching: The Key to Dodging Software Supply Chain Attacks
Supply chain attacks are becoming increasingly popular and frequent as they allow attackers to infect a large number of different organizations by compromising just...










-1.webp)